How to Connect Using AWS CLI: A Step-by-Step Guide
In today's cloud-centric world, managing your AWS infrastructure efficiently is paramount. One of the most powerful tools for …
Shifting Left in AppSec: A Lesson from Benjamin Franklin
In the bustling city of Philadelphia during the 18th century, fire was a constant and terrifying threat. Wooden …
Setting the Trap – A Guide to Integrating Honeypots Into Web Applications
What are Honeypots? A honeypot, in its simplest form, is a decoy system or network designed to attract …
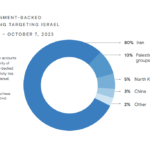
Google TAG’s Analysis on the Israel-Iran-Hamas Cyber Warfare Before and After Oct 7th
Google's Threat Analysis Group (TAG) just released a very interesting analysis of the offensive cyber activities between Israel, …
7 Techniques To Gain Remote Code Execution on Web Applications
Remote Code Execution (RCE) is considered the holy grail in web application security. As a seasoned penetration tester, …
The Four Pillars of Cyber Risk Management
Your organization is a castle, and in this modern age, cyber threats are the besieging army at your …
The Secure Development Life Cycle (SSDLC) – Best Practices for Your Application Security
The Secure Development Life Cycle (SDLC) is an approach to software development that incorporates security measures into each …
What Can Red Teamers Learn From Bug Bounty Hunters
In recent years, the world of cybersecurity has witnessed a dramatic rise in the sophistication and maturity of …
How to Choose the Right Penetration Testing Service
In today's digital age, penetration testing isn’t just a luxury; it's an absolute necessity. But let's face it: …
Unmasking the Great Penetration Testing Deception: Are You a Victim?
In the realm of cybersecurity, penetration testing is a critical element, providing organizations with a proactive approach to …
Red Team Operations vs. Penetration Testing: What’s the Difference?
In the realm of cybersecurity, terms like "Red Team Operations" and "Penetration Testing" are often thrown around interchangeably. …
Common Security Vulnerabilities in Code and How to Prevent Them
In today's digitally driven world, the significance of robust cybersecurity measures cannot be overstated. Every line of code …
The Fundamentals of Secure Coding: Best Practices for Developers
Introduction In the digital age, where software applications are at the heart of daily activities, ensuring their security …
Black Box Penetration testing vs. White Box Penetration Testing Explained
The digital universe is vast, intricate, and continually evolving. To safeguard this cosmos, penetration testing stands as a …
Understanding SSRF Vulnerabilities in the Age of Microservices
For those diving deep into cybersecurity and penetration testing, understanding the complexities and nuances of different vulnerabilities is …
A Penetration Tester’s Guide To Hacking OAuth 2.0 and OpenId Connect Systems
Introduction As the internet evolves, so does the complexity of ensuring secure access and user authentication. Two widely-adopted …
10 Methods to Mitigate Your SaaS Supply Chain Risk
The Problem Over the last few years more and more R&D teams have started to abandon the traditional …
Unique Challenges and Best Practices in Securing SCADA and ICS
Supervisory Control and Data Acquisition (SCADA) and Industrial Control Systems (ICS) play a critical role in managing and …
Squash The Bug Early With Threat Modeling
In the dynamic and ever-evolving landscape of cybersecurity, proactive measures are essential to safeguard organizations from potential threats. …
Common Mistakes to Avoid in Penetration Testing: Tips from Experts
Introduction Penetration testing is a crucial process in identifying and addressing security vulnerabilities within an organization's systems and …
All Blog Posts
- How to Connect Using AWS CLI: A Step-by-Step Guide

- Shifting Left in AppSec: A Lesson from Benjamin Franklin

- Setting the Trap – A Guide to Integrating Honeypots Into Web Applications

- Google TAG’s Analysis on the Israel-Iran-Hamas Cyber Warfare Before and After Oct 7th
- 7 Techniques To Gain Remote Code Execution on Web Applications

- The Four Pillars of Cyber Risk Management

- The Secure Development Life Cycle (SSDLC) – Best Practices for Your Application Security

- What Can Red Teamers Learn From Bug Bounty Hunters

- How to Choose the Right Penetration Testing Service

- Unmasking the Great Penetration Testing Deception: Are You a Victim?

- Red Team Operations vs. Penetration Testing: What’s the Difference?

- Common Security Vulnerabilities in Code and How to Prevent Them

- The Fundamentals of Secure Coding: Best Practices for Developers

- Black Box Penetration testing vs. White Box Penetration Testing Explained

- Understanding SSRF Vulnerabilities in the Age of Microservices

- A Penetration Tester’s Guide To Hacking OAuth 2.0 and OpenId Connect Systems

- 10 Methods to Mitigate Your SaaS Supply Chain Risk

- Unique Challenges and Best Practices in Securing SCADA and ICS

- Squash The Bug Early With Threat Modeling

- Common Mistakes to Avoid in Penetration Testing: Tips from Experts

- Challenges and Trends in Modern Penetration Testing: Staying Ahead in the Cybersecurity Game

