Google’s Threat Analysis Group (TAG) just released a very interesting analysis of the offensive cyber activities between Israel, Iran and Hamas-Linked groups. The research covers offensive activities both leading to Oct 7th and after Oct 7th.
In a recent in-depth analysis by Google’s Threat Analysis Group (TAG), the intricate web of cyber operations involving Israel, Iran, and groups linked to Hamas has been meticulously analyzed. This research, spanning the period before and after October 7th, sheds light on the cyber dynamics and tactics that define this digital battleground.
Key Takeaways:
- There is no evidence that the initial attack on Oct 7th included a planned cyber component. There is also no increase in cyber attacks against Israeli targets prior to Oct 7th, however we do see an increase of attacks after the attack. This suggests that, unsurprisingly, not a lot of threat actors were “in the know” before the attack.
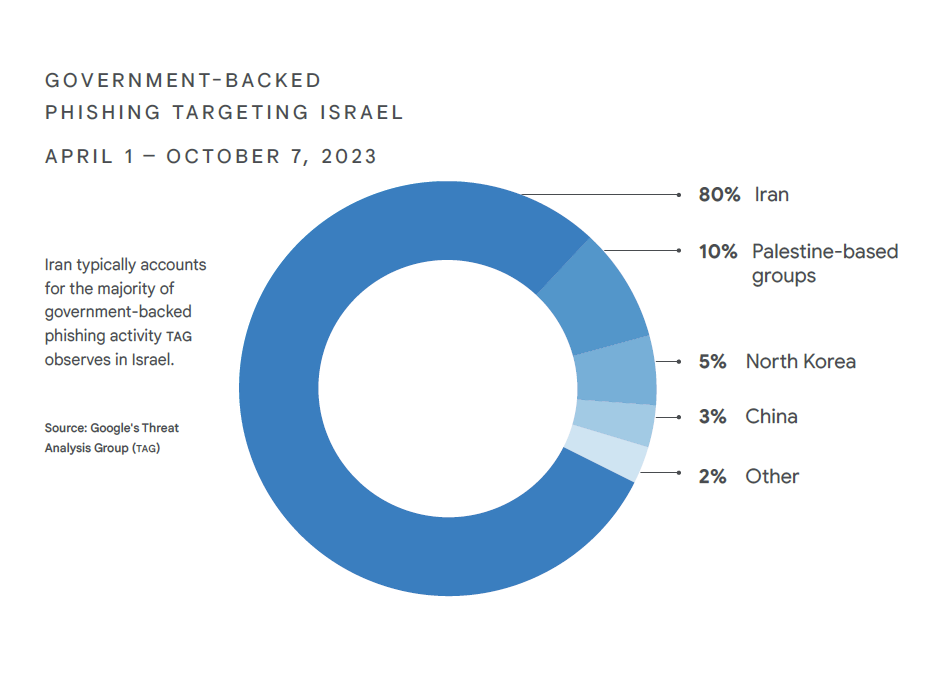
- Iran accounted for approximately 80% of all government-backed phishing activity leading up to Oct 7th, targeting users based in Israel. Pro Palestine hacking groups account for another 10% percent of these attacks.
- Most attacks start as mass phishing campaigns against Israeli targets.
- Most of the attacks are hack-and-leak or wiper operations.
- Prime targets are Military, government, healthcare, financial and energy.
- Initial compromise is usually done VIA phishing and social engineering, then malware is used with basic custom backdoors and widely available remote access tools purchased on underground forums. Only rarely did the researchers find advanced custom malware being deployed.
- Hamas-backed groups also target Fatah members with phishing and malware campaigns.
Iran’s Strategy
According to the research, Iran’s main strategy in its offensive cyber operations, largely didn’t change post Oct 7th. Their main focus remains to demoralize Israeli citizens and erode their trust in national organizations. This is done by leaking PII of civilians and wiping data of targeted organizations. The researchers say that the only change in Iran’s strategy post Oct 7th, is that now we see a focused effort by Iran to undercut public support for the war.
Noteworthy attacks
Even though, most of the documented attacks are of somewhat low technical sophistication, There are two noteworthy attacks described in the article, which I find particularly interesting. These attacks show a more advanced capability the combine creativity and technical prowess.
Targeting Israel Software Engineers
There is at least one Hamas-linked actor, BLACKATOM, that show signs of more advanced capabilities, including elaborate social engineering tailored to software engineers and custom malware developed for Windows, Mac, and Linux. In this attack the group lured Israel freelance software engineers through LinkedIn. The attackers in the campaign posed as recruiters, looking for software engineers willing to take a coding exam. The participating engineers were asked to use a piece of software as part of a coding test. Little did the participants know that the piece of software was actually a malware developed by the attackers . Targets included software engineers in the Israeli military, as well as Israel’s aerospace and defense industry.
“The instructions directed targets to download a Visual Studio project from an attacker-controlled Github or Drive page, add features to the project to prove their coding skills, and then send it back for evaluation. The project appeared to be a benign HR management app, but included a function to download a malicious ZIP, extract the ZIP, and execute malware inside on the target’s system.”
Combining and XSS with a WinRAR CVE
Another interesting attack that was documented started in early September 2023, in which BLACKSTEM group exploited a reflected cross-site scripting (XSS ) vulnerability on the website of the Palestinian Civil Police Force. The link created a browser popup that redirected the visitor to a “news.rar” archive containing an exploit for a known bug (CVE-2023-38831) in the popular Windows file archiver tool WinRAR. The final payload was the MAGNI FI backdoor which took over the victim’s computer.
What We Don’t See
Sometimes, what we don’t see tells us more that what we do see, and what we don’t see in the research is any evidence of highly advanced capabilities such as Zero Day usage of exploitation of highly secure endpoints. This suggests that Iran and its allies either don’t have or choose not to expose any highly advanced Zero Day capabilities. We also rarely see any impressive exploitation of Internet facing assets such as websites, network infrastructure devices , IOTs, that don’t start of from a social engineering vector. There are basically likely 3 explanations for the lack of such evidence:
- Iran does in fact deploy these types of advanced attacks, but the researchers simply didn’t find evidence for that.
- Iran does not have such capabilities. I think this is unlikely, most serious nation state actors do have at the very least some offensive R&D capabilities.
- Iran is choosing not to expose such capabilities unless it absolutely has to. Perhaps they are saving these capabilities for a direct, kinetic conflict with Israel or the US. This strategic ambiguity serves as a critical reminder of the unseen dimensions in cyber warfare.
Conclusion
Google TAG’s analysis offers a rare glimpse into the cyber tactics and strategies employed in the ongoing digital skirmish between Israel, Iran, and Hamas-linked groups. While the battlefield is complex, and riddled with misinformation, understanding these dynamics is crucial for anticipating future cyber threats and preparing against an ever-evolving adversary landscape.
For further details, visit Google’s official blog post on this research.